
Mobile Application Pentesting
What Is Mobile Application Pentesting?
Mobile App Penetration Testing, is a cybersecurity practice focused on assessing the security of mobile applications. It involves evaluating both the client-side (the mobile app itself) and the server-side components that the app interacts with. The primary goal is to identify and address security vulnerabilities that could be exploited by malicious actors.
Contact UsWhy Mobile Application Pentesting is Important?
Mobile Application Pentesting is important for several reasons, as it addresses the unique security challenges associated with mobile applications. Here are key reasons highlighting its importance:
1. Protecting User Data:
Mobile applications often handle sensitive user data, including personal information, credentials, and financial details. Pentesting helps identify and address vulnerabilities.
2. Preventing Unauthorized Access:
Mobile Application Pentesting ensures that authentication and authorization mechanisms are robust, preventing unauthorized users from accessing sensitive functionalities or data within the app.
3. Mitigating Financial Risks:
Security breaches in mobile applications can lead to financial losses, legal consequences, and damage to an organization's reputation. Pentesting helps identify and mitigate security risks.
4. Ensuring Compliance:
Many industries and regulatory standards mandate the security of mobile applications. Mobile App Pentesting helps organizations comply with these standards.
5. Building User Trust:
Users expect mobile applications to be secure and trustworthy. Conducting Pentesting and addressing identified vulnerabilities instills confidence in users, fostering trust and encouraging continued app usage.
6. Identifying and Fixing Vulnerabilities:
Pentesting goes beyond automated scans, employing manual testing techniques to identify complex vulnerabilities that automated tools may overlook.
7. Addressing Platform-Specific Risks:
Different mobile platforms (Android and iOS) have unique security considerations. Mobile App Pentesting is tailored to assess platform-specific risks.
8. Protecting Against Mobile-Specific Threats:
Mobile devices face specific threats such as jailbreaking (iOS) and rooting (Android). Pentesting helps identify and mitigate these threats to ensure the app's security in both rooted and non-rooted environments.
9. Adapting to Evolving Threats:
The mobile threat landscape is dynamic, with new attack vectors emerging regularly. Pentesting allows organizations to stay ahead of evolving threats by continuously.
10. Improving Incident Response Preparedness:
Pentesting simulates real-world attack scenarios, providing organizations with insights into potential security incidents. This helps improve incident response preparedness.
Bulwarkers Approach to Mobile Application Pentesting:
Unveiling a Strategic Defence Blueprint

1. Information Gathering
Gathering of information through searches of public databases, websites and routing information etc.

2. Scanning
Execution of the scans using automated software tools. Enumeration of hosts, services, application and vulnerabilities.

3. Manual Verification
Verification of the scan results, additional manual discovery and elimination of the false positives.

4. Manual Exploits
Further discovery and exploitation of Manual vulnerabilities using manual Exploits techniques and custom tools an necessary.

5. Analysis and reporting
Analysis of risk and business impact. reporting development of the testing report.

6. Reset and validate
Conduct follow-up testing to verify the effectiveness of remediation efforts and confirm closure of identified vulnerabilities.
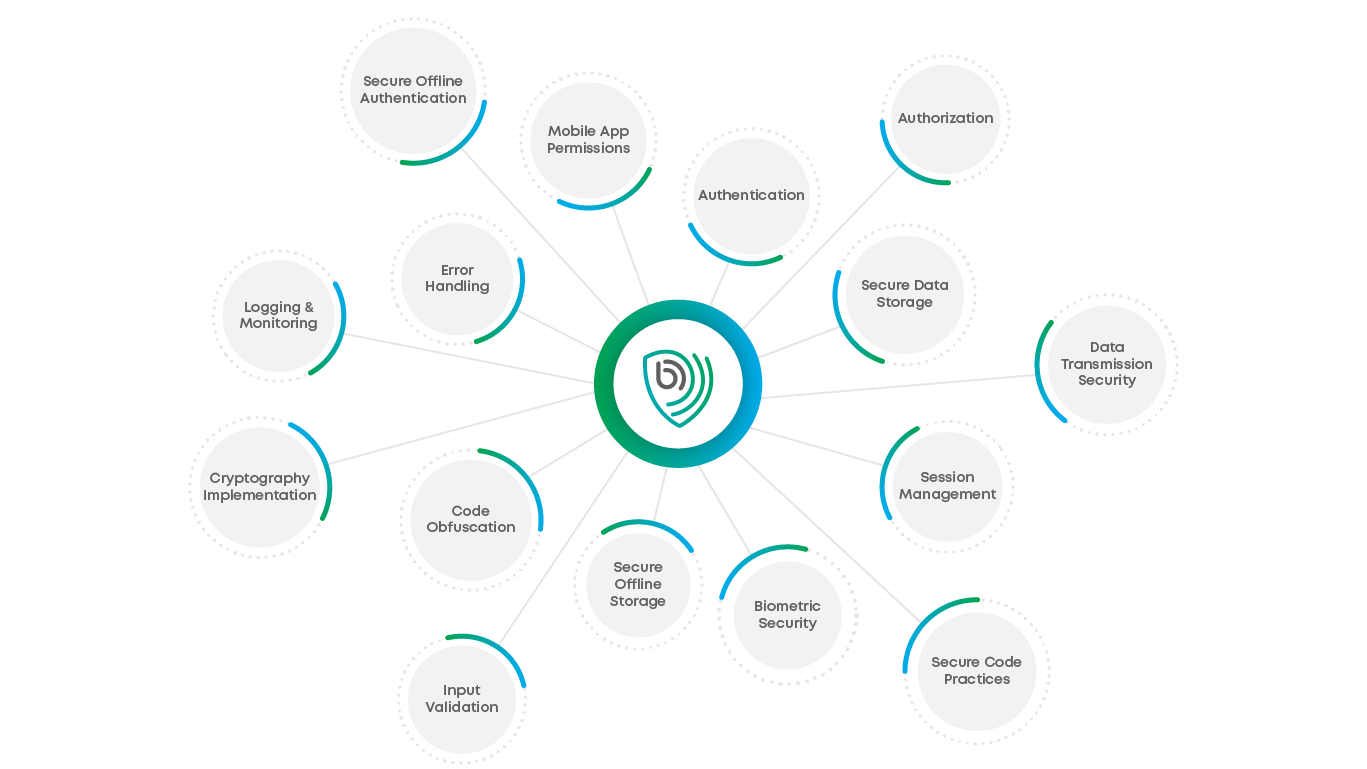
Key Aspects of Mobile Application Pentesting
CERTIFICATE ACKNOWLEDGED BY THE INDUSTRY
Earn your customers' confidence with a distinct, publicly verifiable certificate of security.
Show off your secure application. Have our engineers check your fixes and secure a unique hosting safety certificate for your product.
Distribute the certificate link to your partners and customers to foster trust-based relationships.

Frequently Asked Questions
VAPT stands for Vulnerability Assessment and Penetration Testing. It is a comprehensive cybersecurity approach that combines the identification of vulnerabilities through assessment with the simulation of real-world attacks.
VAPT is crucial for identifying and addressing security vulnerabilities proactively, reducing the risk of cyberattacks, ensuring compliance, and enhancing overall cybersecurity posture.
Vulnerability Assessment focuses on identifying vulnerabilities in a system using automated tools and manual processes. Penetration Testing, on the other hand, actively simulates cyberattacks to test the system's defences and identify potential points of compromise.
VAPT should be conducted regularly, ideally as part of a continuous security program. The frequency depends on factors such as the rate of system changes, industry regulations, and the organization's risk tolerance.
VAPT is typically conducted by cybersecurity professionals, including ethical hackers and certified penetration testers. These individuals have expertise in assessing and securing IT systems.
Common vulnerabilities addressed in VAPT include SQL injection, cross-site scripting (XSS), cross-site request forgery (CSRF), insecure configurations, and vulnerabilities outlined in the OWASP testing guide.
Yes, VAPT can be performed on a variety of systems, including web applications, mobile applications, network infrastructure, and other IT assets.
The duration of a VAPT engagement varies depending on the size and complexity of the system being tested. It can range from a few days to several weeks.
A VAPT report includes details of identified vulnerabilities, their severity levels, exploitation paths for successful attacks, and recommendations for remediation.
While fixing vulnerabilities is crucial, it does not guarantee complete security. Regular assessments, continuous monitoring, and a holistic cybersecurity strategy are essential for maintaining a strong security posture.
In many industries, regulatory standards and compliance requirements mandate regular security assessments, making VAPT an essential component of meeting these standards.
Organizations can benefit from VAPT by reducing the risk of security breaches, ensuring compliance, building user trust, and continually improving their overall cybersecurity resilience.